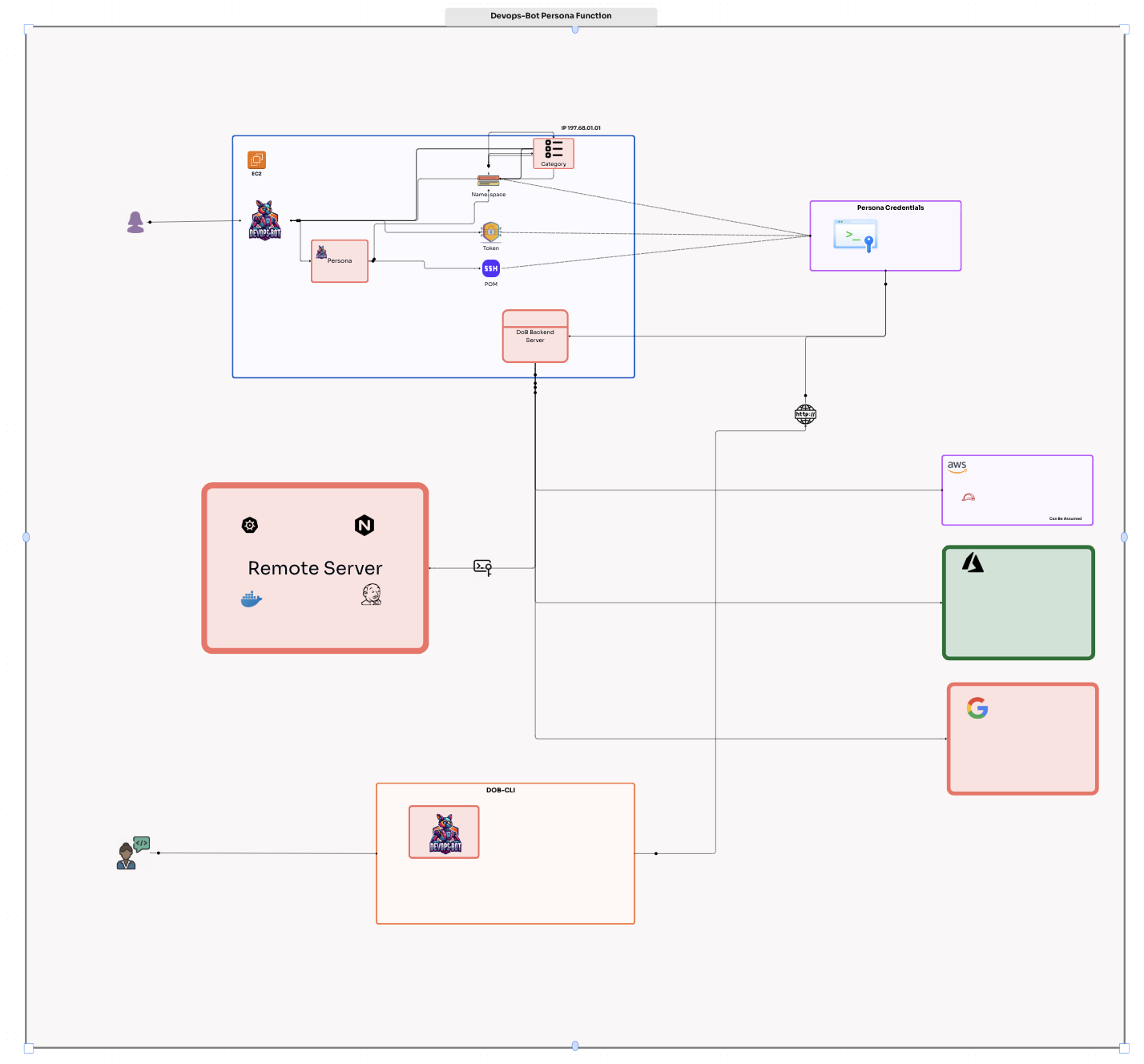
Persona CLI Guide (Integrated with DOB CLI)
The persona CLI, in collaboration with the dob CLI, provides a robust Role-Based Access Control (RBAC) system for remote command execution and configuration management. This guide details its usage, focusing on commands, configurations, and integration workflows.
1. persona config
Description: Configure the remote execution environment by generating a .dobconfig.json file.
Usage:
persona config --persona-name <persona_name> --token <token> \
--private-key-path <private_key_path> --host-endpoint <host_endpoint>Options:
--persona-name: Name of the persona.--token: Token associated with the persona.--private-key-path: Path to the private key PEM file.--host-endpoint: Host endpoint URL (e.g.,http://<public_ip>:<port>).
Details:
- Creates a configuration file at
~/.dobconfig.json. - Stores persona information, token, private key path, and host endpoint for seamless remote command execution.
Example:
persona config --persona-name admin --token abc123 \
--private-key-path ~/keys/admin_key.pem --host-endpoint http://127.0.0.1:8080Output:
- A confirmation message:
Configuration saved to ~/.dobconfig.json.
2. persona run
Description: Proxy any dob command to the host for execution.
Usage:
persona run <dob_command> [--file-path <path_to_file>]Options:
<dob_command>: ThedobCLI command to be executed remotely.--file-path: Optional; specifies a file to be included as inline content.
Details:
- Loads configuration from
~/.dobconfig.json. - Signs the token using the specified private key.
- Sends the command and optional file content to the host endpoint for execution.
- Outputs the execution result.
Example:
persona run create-cluster --region us-east-1 --file-path config.yamlOutput:
- Execution status and response from the host.
Error Handling:
- If
--file-pathis invalid or missing, an error message is displayed. - If the host endpoint is unreachable, the error details are printed.
Configuration File (~/.dobconfig.json)
The configuration file contains the following keys:
{
"persona_name": "<persona_name>",
"token": "<token>",
"private_key_path": "<path_to_private_key>",
"host_endpoint": "<host_endpoint_url>"
}
Example:
{
"persona_name": "admin",
"token": "abc123",
"private_key_path": "/home/user/keys/admin_key.pem",
"host_endpoint": "http://127.0.0.1:8080"
}
Token Signing
The persona CLI uses RSA key pairs to sign tokens for secure communication. The private key specified in the configuration is used to generate a signature.
Function:
def sign_token(private_key_path, token):
with open(private_key_path, "rb") as key_file:
private_key = serialization.load_pem_private_key(key_file.read(), password=None)
signature = private_key.sign(
token.encode(),
padding.PKCS1v15(),
hashes.SHA256()
)
return signature.hex()
Details:
- The signature ensures the integrity of requests sent to the host endpoint.
- Secure RSA keys are required for reliable communication.
Example Workflow
- Configure Persona:
- Run a Command:
- Host Execution:
- View Results:
persona config --persona-name admin --token abc123 \
--private-key-path ~/keys/admin_key.pem --host-endpoint http://127.0.0.1:8080persona run create-cluster --region us-east-1 --file-path cluster.yamlThe command is forwarded to the host endpoint (http://127.0.0.1:8080/execute). The host validates the signature and token before executing the command.
The persona CLI outputs the result from the host.
Error Handling
- Missing Config File:
Error: Config file not found at ~/.dobconfig.json. Please run 'persona config' first.Error: File '<file_path>' not found.Execution failed with status 500: Internal Server ErrorSecurity Considerations
- Private Keys: Ensure that the private key file is securely stored and accessible only to authorized users.
- Token Management: Use unique and time-limited tokens for better security.
- Host Validation: Verify host endpoints to prevent command interception.
This guide ensures you can utilize the persona CLI effectively for secure and controlled remote command execution with dob. For additional support, consult the documentation or contact your system administrator.